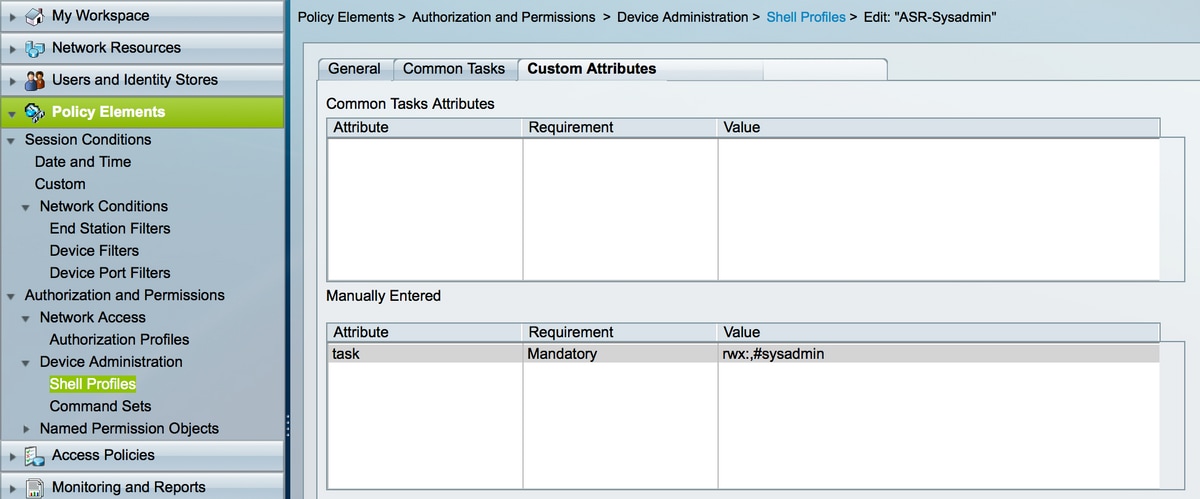
![User Guide for Cisco Secure Access Control System 5.8 - Understanding ACS Policy Model [Cisco Secure Access Control System] - Cisco User Guide for Cisco Secure Access Control System 5.8 - Understanding ACS Policy Model [Cisco Secure Access Control System] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/200001-300000/250001-260000/252001-253000/252958.tif/_jcr_content/renditions/252958.jpg)
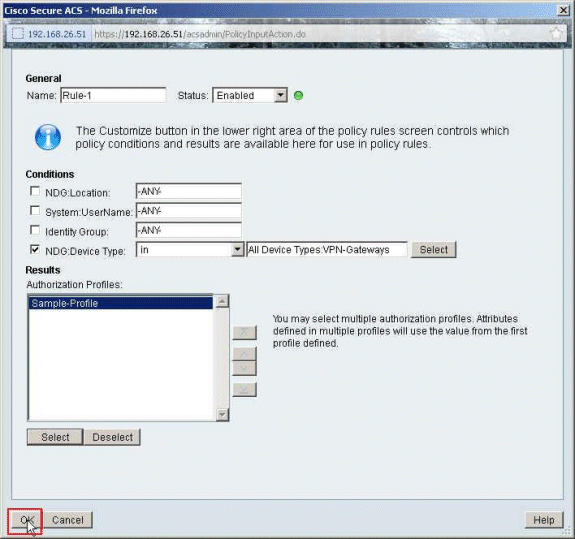
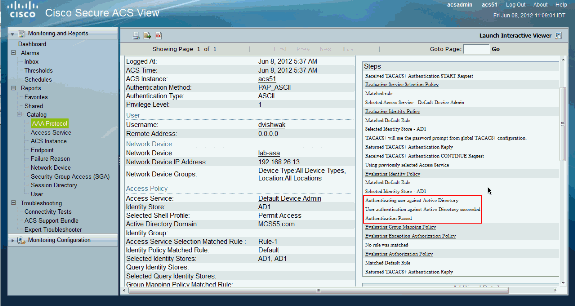
User Guide for Cisco Secure Access Control System 5.8 - Understanding ACS Policy Model [Cisco Secure Access Control System] - Cisco
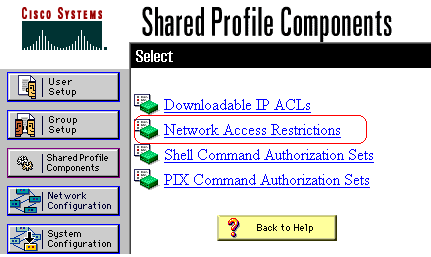
![User Guide for Cisco Secure Access Control System 5.8 - Understanding ACS Policy Model [Cisco Secure Access Control System] - Cisco User Guide for Cisco Secure Access Control System 5.8 - Understanding ACS Policy Model [Cisco Secure Access Control System] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/200001-300000/250001-260000/252001-253000/252961.tif/_jcr_content/renditions/252961.jpg)
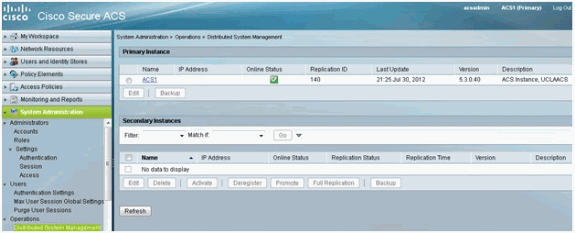
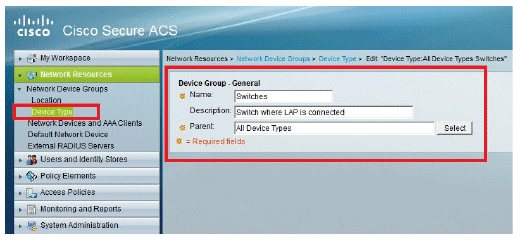
User Guide for Cisco Secure Access Control System 5.8 - Understanding ACS Policy Model [Cisco Secure Access Control System] - Cisco
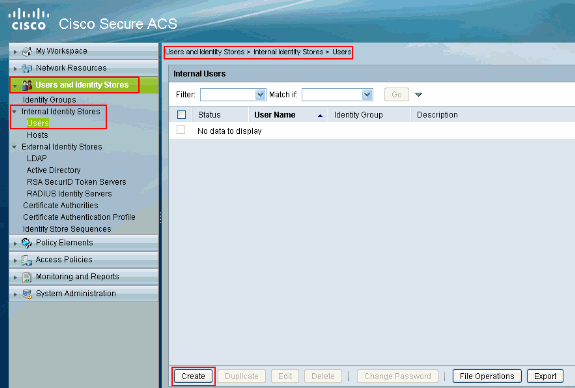
![User Guide for Cisco secure Access Control System 5.8.1 - Understanding Logging [Cisco Secure Access Control System] - Cisco User Guide for Cisco secure Access Control System 5.8.1 - Understanding Logging [Cisco Secure Access Control System] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/200001-300000/200001-210000/204001-205000/204726.tif/_jcr_content/renditions/204726.jpg)
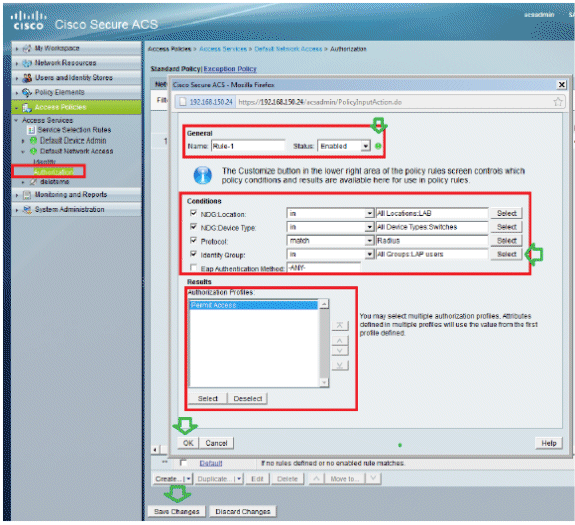
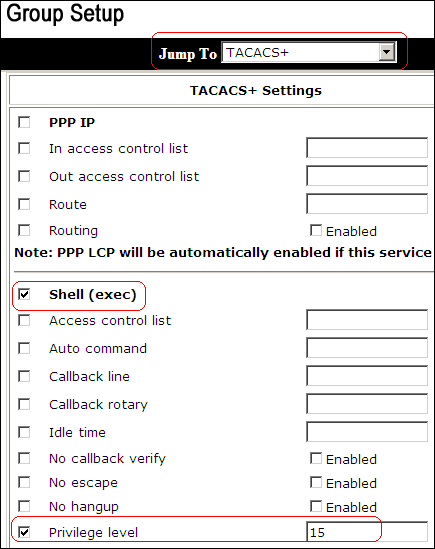
User Guide for Cisco secure Access Control System 5.8.1 - Understanding Logging [Cisco Secure Access Control System] - Cisco
![Migration Guide for Cisco Secure Access Control System 5.8 - Using the Migration Utility to Migrate Data from ACS 4.x to ACS 5.8 [Cisco Secure Access Control System] - Cisco Migration Guide for Cisco Secure Access Control System 5.8 - Using the Migration Utility to Migrate Data from ACS 4.x to ACS 5.8 [Cisco Secure Access Control System] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/100001-200000/190001-200000/195001-196000/195146.tif/_jcr_content/renditions/195146.jpg)
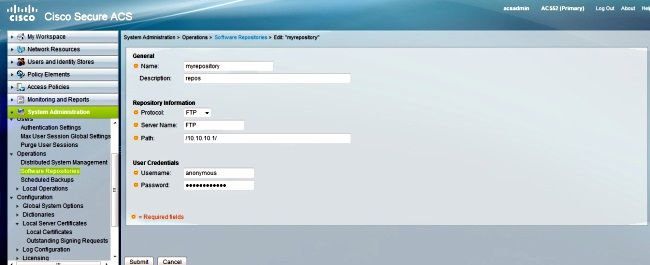
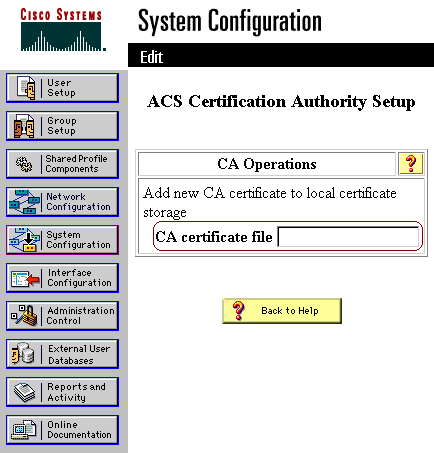
Migration Guide for Cisco Secure Access Control System 5.8 - Using the Migration Utility to Migrate Data from ACS 4.x to ACS 5.8 [Cisco Secure Access Control System] - Cisco
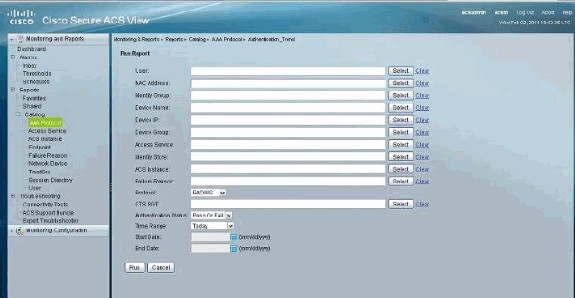
![User Guide for Cisco Secure Access Control System 5.8 - Managing Reports [ Cisco Secure Access Control System] - Cisco User Guide for Cisco Secure Access Control System 5.8 - Managing Reports [ Cisco Secure Access Control System] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/300001-400000/370001-380000/373001-374000/373660.tif/_jcr_content/renditions/373660.jpg)
User Guide for Cisco Secure Access Control System 5.8 - Managing Reports [ Cisco Secure Access Control System] - Cisco